In the digital age, safeguarding your online privacy and security has become increasingly crucial. A virtual private network (VPN) is a powerful tool that can help you achieve this. VPNs create a secure, encrypted connection between your device and the internet, shielding your online activities from prying eyes and potential cyber threats.
What is a VPN ? VPNs are essential for protecting your data and maintaining your privacy in 2025 and beyond. They prevent your internet service provider (ISP) from monitoring and logging your online activities, and also prevent other actors from tracking your activity down to your specific device. This is because a VPN makes it appear as if you are accessing the internet from the IP address of your VPN server, rather than your device’s specific IP address.
By using a VPN, you can browse the web securely, access geo-restricted content, and even bypass censorship, all while keeping your real identity and location hidden. In today’s digital landscape, where cybersecurity threats are on the rise and online privacy is under constant scrutiny, a reliable VPN is a must-have tool for anyone who values their digital safety and freedom.
Key Takeaways
- A VPN creates a secure, encrypted connection between your device and the internet, protecting your online privacy and security.
- VPNs prevent your ISP from monitoring and logging your online activities, and hide your IP address to prevent tracking.
- VPNs are essential for secure remote access, bypassing censorship, and accessing geo-restricted content.
- Choosing a reliable VPN with robust security features is crucial for ensuring your online safety and privacy.
- VPNs are becoming increasingly important in the digital age, as cybersecurity threats and online privacy concerns continue to grow.
Introduction to VPNs
Importance of Using a VPN
Using a virtual private network (VPN) is crucial for securing your online activities, particularly when accessing public Wi-Fi networks or working remotely. VPNs create a secure, encrypted connection that protects your data from cybercriminals and other third parties who may be monitoring your internet traffic. This is especially important when conducting sensitive transactions or accessing confidential information, as a VPN can prevent your personal and financial data from being intercepted.
What is a VPN?
A VPN is a technology that establishes a secure and encrypted connection over a less secure network, such as the internet. It allows users to connect to a private network remotely, as if they were physically present on the local network. VPNs work by routing your internet traffic through an encrypted tunnel, masking your IP address and hiding your online activities from your internet service provider and other third-party observers.
The increasing need for online security and privacy has led to a rise in VPN adoption, with users seeking protection while browsing on public Wi-Fi and accessing geo-locked content. VPNs employ various encryption protocols, such as OpenVPN, SSTP, IKEv2/IPSec, and WireGuard, to ensure the confidentiality and security of user data.
| Encryption Protocol | Features |
|---|---|
| OpenVPN | 256-bit AES encryption using OpenSSL, tunneling through TCP and UDP, SSL/TSL certifications |
| SSTP | 256-bit encryption, SSL/TSL certifications, natively built into Windows OS |
| IKEv2/IPSec | Recommended for mobile VPNs, maintains connections under unstable internet conditions |
| L2TP/IPSec | Basic setup ease, added security when used with IPSec |
| WireGuard | Modern encryption technology, leaner codebase, mobile compatibility |
When choosing a VPN, it’s important to consider factors such as budget, data usage, required geographical locations, and the trustworthiness of the service provider. Checking online reviews and the provider’s reputation can also help ensure user satisfaction and data security.

“A VPN is a must-have for anyone who values their online privacy and security, especially in today’s digital landscape.”
How Does a VPN Work?
To understand how a VPN works, it’s important to first consider how internet transactions occur without the use of a VPN. When you send sensitive information, such as financial details, over a public network, your data is vulnerable to interception by hackers. Your IP address and the information you transmit are visible to anyone monitoring the network traffic, making you susceptible to cyberattacks and data theft.
However, when you use a VPN, your internet traffic is routed through an encrypted tunnel, protecting your data from being intercepted. The VPN client on your device connects to a VPN server, which then connects to the destination server, such as your bank’s server. The VPN encrypts your information and changes your IP address, making it appear as if the transaction is originating from the VPN server’s location, rather than your own. This ensures your online activities and personal information remain secure and anonymous.
A Transaction Without Using a VPN
- Your device connects directly to the internet, exposing your IP address and unencrypted data.
- Your sensitive information, such as bank details, is transmitted over the public network.
- Hackers can intercept and access your personal data, putting you at risk of identity theft and financial fraud.
A Transaction Using a VPN
- Your device connects to a VPN server, which then connects to the destination server.
- The VPN encrypts your information and changes your IP address, masking your true identity and location.
- Your data is transmitted securely through the encrypted VPN tunnel, protecting it from unauthorized access.
By using a VPN, you can enjoy the benefits of anonymous browsing, encrypted connection, and enhanced public network security when conducting internet transactions. This ensures your how VPN works and how VPN works to safeguard your online activities.

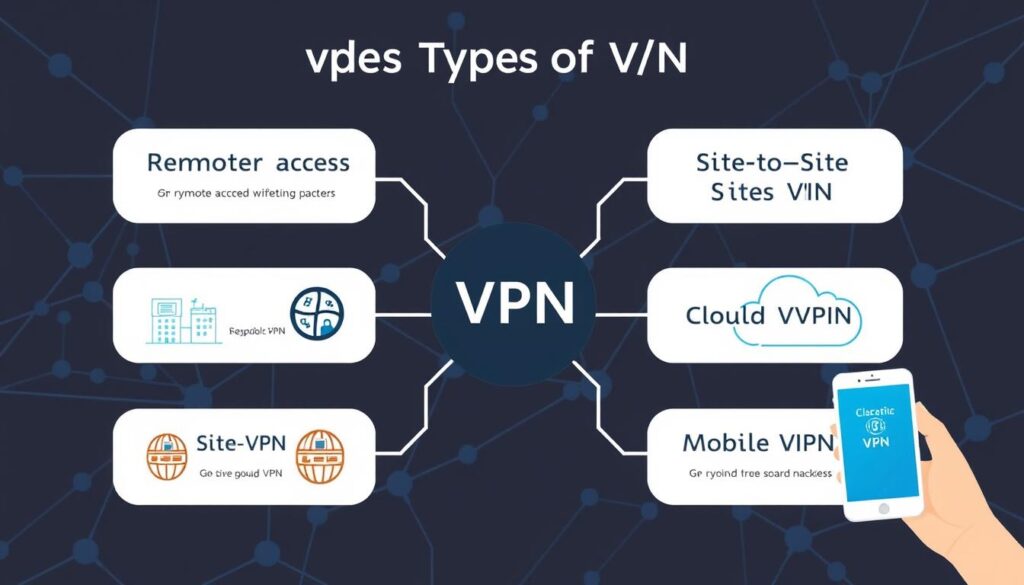
Types of VPNs
When it comes to virtual private networks (VPNs), there are several distinct types that cater to different business needs and use cases. The two main categories of VPNs are remote access VPNs and site-to-site VPNs. Remote access VPNs allow individual users to securely connect their devices to a private network, enabling secure remote access to resources and applications. Site-to-site VPNs, on the other hand, are used to connect multiple offices or locations of a company, allowing them to share information and resources securely over the internet.
Within these broad categories, there are further sub-types of VPNs. Intranet-based VPNs are used to connect multiple offices of the same company, while Extranet-based VPNs are used to connect companies to each other without direct access to each other’s networks. Cloud VPNs are designed for secure access to cloud-based services, while mobile VPNs cater to the needs of users on the go.
VPNs can also be classified by the protocol they use, such as SSL VPNs, PPTP VPNs, L2TP VPNs, OpenVPN, and others. Each protocol has its own strengths and weaknesses, and the choice of protocol can significantly impact the overall security and performance of the VPN.
| VPN Type | Description |
|---|---|
| Remote Access VPN | Allows individual users to securely connect their devices to a private network, enabling remote access to resources and applications. |
| Site-to-Site VPN | Connects multiple offices or locations of a company, allowing them to share information and resources securely over the internet. |
| Intranet VPN | Used to connect multiple offices of the same company. |
| Extranet VPN | Used to connect companies to each other without direct access to each other’s networks. |
| Cloud VPN | Designed for secure access to cloud-based services. |
| Mobile VPN | Catered to the needs of users on the go. |
Regardless of the specific type, VPNs play a crucial role in ensuring secure and private communication, whether for individual users or entire organizations. By understanding the different types of VPNs and their capabilities, businesses can make informed decisions to address their unique security and connectivity requirements.
What is a VPN
A VPN, or virtual private network, is a powerful technology that creates a secure and encrypted connection over a less secure network, such as the internet. It allows users to connect to a private network remotely, as if they were physically present on the local network.
VPNs work by routing your internet traffic through an encrypted tunnel, masking your IP address and hiding your online activities from your internet service provider and other third-party observers. This provides an additional layer of privacy and security, making it an essential tool for individuals and businesses alike.
The VPN technology operates by authenticating the client, applying encryption protocols, creating an encrypted tunnel over the internet, wrapping data packets in an outer packet for secure transfer, and decrypting data upon arrival at the server. This process ensures that your VPN definition and online activities remain confidential and protected from prying eyes.
| Key VPN Features | Benefits |
|---|---|
| Encryption Protocols | Provides varying levels of privacy and speed |
| IP Address Masking | Hides your real IP address, enhancing online anonymity |
| Secure Tunneling | Encrypts and protects your internet traffic from third-party monitoring |
| Remote Access | Allows you to connect to a private network from anywhere |
The what is a VPN concept is crucial for individuals and businesses seeking to enhance their online privacy, security, and accessibility, whether they’re accessing sensitive information, bypassing censorship, or simply browsing the web securely.
“VPNs provide a layer of online privacy but do not guarantee complete anonymity.”
Applications of VPNs
Virtual Private Networks (VPNs) have become an indispensable tool in the digital age, offering a wide range of applications to enhance online security, privacy, and accessibility. From securing remote access for businesses to bypassing censorship and geo-restrictions, VPNs have proven invaluable in today’s interconnected world.
Secure Remote Access
VPNs are widely used to provide secure remote access, allowing employees to securely connect to their company’s private network from anywhere in the world. This is particularly important for businesses with remote workers or employees who need to access sensitive information while traveling. By establishing a secure, encrypted connection, VPNs ensure that sensitive data remains protected, even on public networks.
Bypass Censorship and Geo-restrictions
VPNs also enable users to bypass censorship and geo-restrictions, allowing them to access content and websites that may be blocked in their region. By connecting to a VPN server located in a different country, users can effectively spoof their geographic location and access content that may be restricted in their home region. This is particularly useful for individuals living in countries with strict internet censorship, as well as for accessing region-locked streaming content, online gaming servers, or other services that are limited based on the user’s location.
The versatility of VPNs extends beyond these key applications, making them invaluable tools for individuals and businesses alike. Whether you’re seeking to secure your online activities, bypass restrictions, or access restricted content, a reliable VPN can be a game-changer in the digital landscape.
| VPN Feature | Description |
|---|---|
| Kill Switch | Automatically disconnects the device from the internet if the VPN connection is lost, preventing data exposure. |
| Split Tunneling | Allows certain apps or websites to bypass the VPN, while others are routed through the secure connection. |
| Multihop Technology | Routes the VPN connection through multiple servers, adding an extra layer of security and anonymity. |
| Camouflage Mode | Disguises the VPN traffic to appear as regular internet traffic, bypassing detection by internet service providers. |
| P2P Configured Servers | Optimized servers for secure file sharing and torrenting activities. |

“VPNs have become essential tools in the digital age, empowering users to securely access the internet, bypass restrictions, and protect their online activities.”
Choosing the Right VPN
When selecting a VPN, it’s crucial to look for specific features that ensure maximum security and privacy. These include robust encryption mechanisms, a vast network of VPN servers around the world, support for secure protocols like OpenVPN or WireGuard, and a clear, transparent privacy policy.
Features to Look for in a VPN
The top-rated VPN services, such as NordVPN (4.5 rating), Surfshark VPN (4.0 rating), Proton VPN (5.0 rating), TunnelBear VPN (4.0 rating), Mullvad VPN (4.5 rating), and IVPN (4.0 rating), offer a range of essential features:
- Encryption: Strong encryption protocols like AES-256 and secure key exchange algorithms like RSA-4096/RSA-2048 to protect your data from prying eyes.
- Server Coverage: A wide network of VPN servers across multiple countries to reduce server load and provide more options for bypassing geographic restrictions.
- Protocols: Support for industry-standard VPN protocols like OpenVPN and the newer, more secure WireGuard protocol.
- Privacy Policy: A clear, transparent privacy policy that outlines the VPN provider’s data-logging practices and commitment to user privacy.
- Additional Features: A “kill switch” to terminate your internet connection if the VPN service is interrupted, and the ability to cover multiple devices under a single subscription.
The Federal Trade Commission’s 2021 report highlighted the significant amount of detailed online activity data that internet service providers (ISPs) have on users, underscoring the need for VPNs to enhance privacy. While VPNs do not provide total anonymity, they can effectively mask your IP address and make it harder for advertisers to track your online activities through methods like browser fingerprinting.
When choosing a VPN, it’s essential to prioritize security, privacy, and transparency to ensure your online activities remain protected and your personal information is safeguarded.

Conclusion
In the ever-evolving digital landscape of 2025, the use of Virtual Private Networks (VPNs) has become indispensable for maintaining online privacy and security. By establishing a secure, encrypted connection between your device and the internet, a VPN safeguards your data from the prying eyes of cybercriminals, government surveillance, and other threats that can compromise your digital footprint.
Whether you’re a remote worker accessing sensitive information, a passionate streamer seeking to bypass geographic restrictions, or simply a conscious internet user, a reliable VPN has become a must-have tool for ensuring your online privacy and security. With the growing importance of VPN importance in our daily digital lives, the adoption of this technology will only continue to rise, empowering individuals and organizations alike to navigate the online world with confidence and peace of mind.
As we move forward, the significance of VPNs will only become more pronounced, making them an essential component of our digital security arsenal in 2025 and beyond. By embracing this transformative technology, we can take control of our online presence, safeguard our sensitive information, and unlock the full potential of the internet while navigating the digital landscape with unparalleled security and privacy.
FAQ
What is a VPN?
A virtual private network (VPN) is a secure connection between your computer and your desired destination on the internet. It acts as an anonymous middleman that allows you to browse privately and securely, encrypting your data and masking your location.
How does a VPN work?
A VPN works by routing your internet traffic through an encrypted tunnel, masking your IP address and hiding your online activities from your internet service provider and other third-party observers. This ensures your online activities and personal information remain secure and anonymous.
Why is using a VPN important?
Using a VPN is crucial for securing your online activities, especially when using public Wi-Fi networks or working remotely. VPNs establish a secure, encrypted connection that protects your data from cybercriminals and other third parties who may be monitoring your internet traffic.
What are the different types of VPNs?
There are primarily two main types of VPNs: remote access VPNs and site-to-site VPNs. Remote access VPNs allow users to securely connect their devices to a private network, enabling remote access to resources and applications. Site-to-site VPNs are used to connect multiple offices or locations of a company, allowing them to share information and resources securely over the internet.
How can a VPN be used to bypass censorship and geo-restrictions?
VPNs can be used to bypass censorship and geo-restrictions imposed by governments or content providers. By connecting to a VPN server located in a different country, users can effectively spoof their geographic location and access content that may be restricted in their home region.
What features should I look for when choosing a VPN?
When selecting a VPN, it’s important to look for certain key features to ensure maximum security and privacy. These include strong encryption mechanisms, a wide network of VPN servers around the world, support for secure protocols like OpenVPN or WireGuard, an additional layer of protection through shared IP addresses, and a clear and transparent privacy policy.


















